Using SSH: Secure Tunnels for the Common Man: Part I
In honor of the release of Chris Seibold's Big Book of Apple Hacks, here is a variation on a hack that appears in the book. Enjoy!
Secure Shell or SSH is a network protocol that provides secure communication between two computers. If SSH is used correctly, no eavesdropping or tampering with your data is possible, unless you are under attack by an immortal miscreant with extraordinarily powerful computers.
SSH is available in many forms -- as proprietary, open source, and free software from a variety of organizations. The most popular implementation is OpenSSH and this is the one that is part of Mac OS X.
Typically, SSH is used to securely log in to remote machines in order to execute commands. You can also use this secure connection to transfer files, run GUI programs under X windows, and forward ports. It is this last feature that will enable us to create secure tunnels between computers.
Tunnels: What and Why?
The purpose of an SSH tunnel is to secure the "last mile" of your connection. There are many reasons to want this, but the most common are in situations where your connection is monitored, restricted, or not secure. For example, if you are at a coffee shop using your laptop over the provided unencrypted WiFi connection, there is a chance that someone is eavesdropping on your communication. In such a situation, you could create a tunnel to a home machine to check your email securely.
Also, many people have certain kinds of applications or sites blocked or monitored by their place of work (or by their country). Setting up an SSH tunnel to a machine outside your work (or country) network will allow you to keep your communication private and to use applications that may otherwise be blocked.
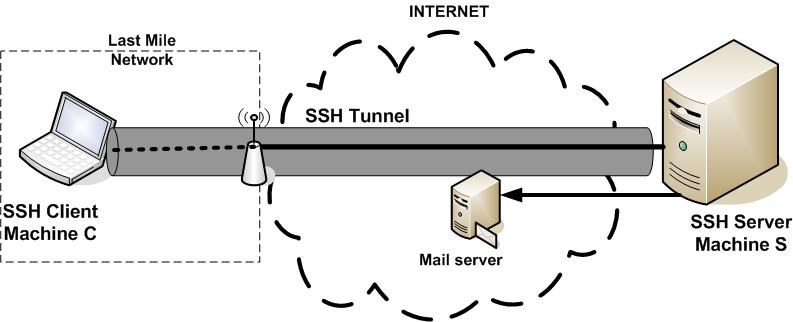
To set up an SSH tunnel, you require two computers -- one as the SSH client (machine C) and another as the SSH server (machine S). Machine C is insecure or restricted, while Machine S has full access to the Internet and is preferably under your control. In the example of an insecure wireless computer, Machine C is your wireless laptop and Machine S is a desktop connected to the Internet. In the example of securing your work communication, Machine C would be your work computer and Machine S could be a home computer connected to the Internet.
In order to set up an SSH tunnel, you will need the following:
- Two machines with SSH installed. Mac OS X comes with SSH, as do most variants of Unix and Linux. Windows users can try out Cygwin.
- At least one of which has "Remote Login" enabled (or SSH server configured for non-Mac machines). This can be done through the "Sharing" preference under "System Preferences."
- An Internet available Internet Protocol (IP) address for the server machine. Most broadband connections provide a unique IP for your home, though it may change frequently. You can find your global IP under the "Network" section of "System Preferences" if you are directly connected to your cable/DSL modem. If you are connected through a wireless router, you can find your IP in the administration interface for that device. An IP is a unique address for a machine that is accessible from anywhere on the Internet and is of the form w.x.y.z (where w, x, y and z are numbers between 0 and 255). You can also get a hostname for your IP address at services such as DynDNS.com.
You can prepare those resources, and in the next part of this article next week I will help you build the SSH tunnel.


Comments
I do not believe that something is absolutely safe in this world. Although the use of tunnels as you mentioned. However, it is worth trying. aisle marking
Learn how to hack an application is something fun. In my opinion, as long as done with responsibility, there is no harm for us to learning about this sort of thing.
Prostate Stimulation
The ability of apple was no need to bargain anymore. I think this could really give a good solution on this issue. Accounting Sydney
Weight of 34.000 tons. Can you imagine the weight once. Surely this freighter will be of great help smooth transportation of goods delivery. Body Oil
I am not a Mac user, therefore, I do not know whether this is an important thing or just an ordinary problems. Electronic Medical Records Companies
I do not use Apple computers. So I do not know the main function of this. Therefore, I will tell my friends. I’m sure they would be interested. Wedding Gifts
Maintenance for machines is very needed. It will prevent the machine from broken too fast.
formal dresses for girls
I know that he must have been considered very successful for the role he has been playing as a good pianist. And this shows in the appreciate shown by Sony Entertainment which offers him a good long term contract. 642-427/642-642/642-617/642-637/646-578/350-029/642-647/642-982/650-177/646-046
It is true that the apple has become an integral part of technological progress. Therefore, the apple has its own market share, and also a loyal admirer. Online flash games
I agree with the entire comment above. Thanks for sharing nice information with us. i like your post and all you share with us is uptodate and quite informative, i would like to bookmark the page so i can come here again to read you, as you have done a wonderful job.
ingersoll rand air compressor | husky air compressor.
Many do not I know about Macs. Since I’m not a user of this tool. Any information is good information here.
outdoor patio
Quite exciting for me to know and learn about this article. I feel that this article is an excellent teacher. logbook loan today
I was planning to buy a Mac in the near future. Therefore, I’m finding out as much as possible about the Mac. secure vpn
I can this technique is worth to try, even if we can’t do it properly. It will be our advantages to know about this a little. Hope so.
Property Valuation Perth
I’ve read through a number of the articles in your website , and I love the way you blog. I included it to my favorites blog site list and will also be checking quickly. Cheap Taylor Swift Tickets || Cheap Journey Tickets